What is ISAE3000 SOC 2 and why is it important?
LeadDesk is ISAE3000 SOC 2 Type I accredited by KPMG. But what does this actually mean for you and why is it important?
schedule5 minute read
LeadDesk is ISAE3000 SOC 2 Type I accredited by KPMG. But what does this actually mean for you and why is it important?
Why should I care about SOC 2?
ISAE3000 SOC 2 (SOC 2) conformity is a must-have requirement for any security-conscious business buying an external service, particularly when you’re dealing with personally identifiable information.
Government Bodies, Agencies and Enterprise Companies
When you are drafting a Request for Information or Request for Proposal (RFI/RFP) for a service, the minimum requirement is often either SOC 2 accreditation or ISO 27001 certification, or both.
[LeadDesk also has ISO 27001 Certification – Read More Here]
Small and Medium Companies
If you’re working in a particularly data-sensitive industry, like healthcare, you need to consider how your information is handled by the services you use.
In summary, if you care about keeping your customer information secure across all your services, only choose services with SOC 2 accreditation and/or ISO 27001 certification.
“With SOC2, LeadDesk can assure our customers that our services are built and managed in accordance with one of the most recognized security standards in the world.” – Trang Nguyen, Internal Auditor at LeadDesk
What is SOC 2?
Systems and Organizational Controls (SOC) are reports made by an independent auditor after evaluating how a company handles customer data, particularly sensitive data, in their everyday procedures.
SOC 2 accreditation is issued under the International Standard on Assurance Engagement (ISAE).
LeadDesk was audited by KPMG for ISAE3000 SOC 2 Type I accreditation. Type I describes if a company has the capability to meet certain trust principles and criteria as a service provider. Type II describes the effectiveness of these capabilities in operation.
How do you get SOC 2 accreditation?
SOC 2 accreditation comes in two parts. In its most basic form, the organisation must show that they are able to fulfil 17 requirements of what is known as the COSO framework’s Principles of Internal Control. The other part covers optional Trust Service Criteria summarised below.
SOC 2 Requirement: The 17 Principles of Internal Control
The 17 Principles of Internal Control are mandatory and must be completed by every organisation looking for SOC 2 accreditation. In addition, there are 4 extra factors that can also be evaluated.
These principles ensure that the company has procedures in place to keep information secure, to make sure only relevant employees have access to confidential information, and to minimise risks through continuous training, system monitoring and consistent evaluation of partners and third-party vendors.
This means that a company that has passed the requirements of the Principles of Control:
- Trains all their employees in information security.
- Makes sure anyone they purchase services from have similar information security protocols.
- Ensures all customer data is secure, backed-up and restricts physical and digital access to that data. And removes this data at the end of a customer relationship.
- Has procedures in place to rapidly respond to any incidents.
- Regularly audits information security procedures internally, and with an external auditor.
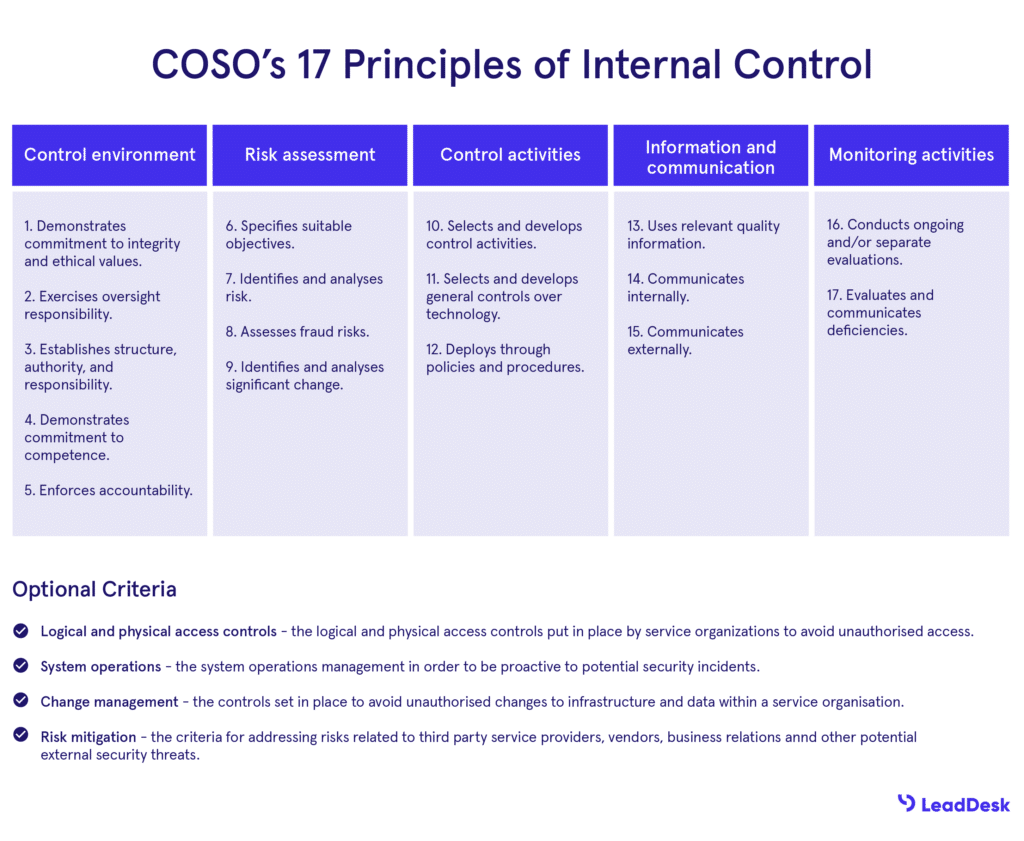
COSO’s 17 Principles of Control, image adapted from CGCompliance.
The 5 Trust Service Criteria
If an organisation can show that they meet the 17 Principles of Internal control, they can also optionally choose to be examined for any, or all of, the five Trust Service Criteria for SOC 2 accreditation. In this part, the company can choose which of the five criteria are most applicable to their business.
The Trust Service Criteria cover how a company handles customer data by examining:
1. Security
This includes firewalls, intrusion detection and whether the company uses multi-factor authentication in its services.
Passing these requirements in a SOC 2 audit means that LeadDesk has minimised the possibility of data leaks and security breaches.
2. Availability
Companies providing critical business services need to be reliable and available. Their customers need the peace of mind that any issues are fixed quickly, and won’t adversely affect their business.
In the audit, LeadDesk was examined for how we monitor our software availability, and how we respond to, and recover from incidents if they happen.
3. Confidentiality
Auditors examine how the company works to keep data confidential. This includes access controls so only a select group of people have access to the data. Examples might include business plans, intellectual property and sensitive financial information.
LeadDesk was also examined for how data it processes is encrypted to prevent any unauthorised access in transit.
4. Processing integrity
Does the system being audited keep your data pure and unaltered? Processing integrity requires that data will only be processed when authorised, and will not distort or change the data.
When examining processing integrity, auditors look at quality assurance practises and process monitoring.
5. Privacy
Personally Identifiable Information should always be handled carefully by any organisation. Previously mentioned factors like encryption, multi-factor authentication and access control all play a part in keeping such information private. Auditors will check for these factors when examining privacy under SOC 2.
In addition to the 17 COSO framework requirements, LeadDesk was evaluated for the three Trust Service Criteria most applicable to our organisation: Security, Availability and Confidentiality.
What’s the difference between SOC 2 and ISO 27001?
SOC 2 and ISO 27001 do have some similarities, but there are some key differences in how they examine a company’s security controls:
| ISO27001 | ISAE3000/SOC 2 | |
| What | International Standard for Information Security | Controls on Trust Service Criteria and Criteria for Security |
| Deliverable | A certificate confirming the organisation has met the requirements of the standard. | Full report based on tests performed by the auditor, with an attestation that the company has passed under agreed criteria. |
| Assurance coverage | Security only | Security and optional criteria (e.g. Availability, Confidentiality, Security) |
| Focus | Design of security controls. | How effective the security controls are. |
If you would like to learn more about why LeadDesk is the most secure solution for your contact center software, book a demo.